Solar plant owners urged to include cyber security in O&M contracts
Cyber security management should be implemented in solar operations and maintenance (O&M) contracts to maximize the effectiveness of pre-handover measures and rigorous security inventories, Jon Franzino, Director of Grid Security at Grid Subject Matter Experts (GridSME), said.

Related Articles
Electricity generators and grid operators are placing an increasing emphasis on cyber security as plants become more integrated with grid services and the internet.
Solar plant owners should use a combination of proactive measures during the construction phase, employee awareness strategies and effective system updates, to reduce cyber security risks cost-effectively, Jon Franzino, Director of Grid Security at Grid Subject Matter Experts (GridSME), told the New Energy Update PV O&M USA conference on November 2.
"Cyber security is not a one and done static thing...You have to get up in front of it and then you have to give it the care and...update it," he said.
Solar plant owners should look to implement cyber security management into operations and maintenance (O&M) contracts, for example detailing the installation of patches against the latest threats, Franzino said.
"I have yet to see an O&M contract that addressed network management or network security in any way shape or form...that's actually a huge gap right now," he said.
Global threat
Recent attacks on electricity network assets-- reportedly from Russian and North Korean sources-- show that power generators must be prepared for targeted, as well as blanket, attacks, Franzino told the conference.
"Now we are not just targets of opportunity, we are actually directly targeted. This is backed up with a lot of intelligence and data," he said.
Power blackouts in Ukraine in December 2015 and 2016 have been blamed on cyber attacks on the electricity grid. Hackers disrupted the power system feeding parts of the capital Kiev, reportedly through remote control of SCADA and substation infrastructure.
In September, cyber security firm Symantec said it believed a sophisticated cyber espionage group known as Dragonfly was behind a recent wave of cyber attacks on European and U.S. power generation companies. Targets reportedly included personnel working for power generation companies and manufacturers of plant control systems.
According to the United States Computer Emergency Readiness Team (UC-CERT), the cyber attackers used a variety of methods:
Recent cyber attack tactics, techniques and procedures (TTPs)
• Open-source reconnaissance
• Spear-phishing emails (from compromised legitimate accounts)
• Watering-hole domains
• Host-based exploitation
• Industrial control system (ICS) infrastructure targeting
• Ongoing credential gathering
Source: UC-CERT. For more detail on these tactics, click here.
Vulnerabilities in solar plants have also been identified. In August, Dutch security researcher Willem Westerhof told a conference that hackers could target electricity grids through security flaws in solar power equipment.
According to Westerhof, tests performed on inverters made by SMA group showed hackers could gain remote control of inverter devices and compromise grid stability.
In a response statement, SMA said these risks were found on only four inverter types and customers following recommended installation and operations practices would not be exposed to these risks.
SMA would provide “a firmware update for the four device families to address this issue," it said.
Cyber defense
An important initial step to understanding the cyber risks of a solar plant is to conduct a full inventory of software and hardware vulnerabilities, Franzino said.
This inventory allows operators to build the cyber security strategy which suits the plant specifications, he said.
"You don't need a gold-plated system everywhere, but you do need to look at this from a risk perspective," he said.
Before the handover from construction to operations, owners should look to acquire full cyber security documentation from the EPC company, including the latest configuration backups and server images of the systems, Franzino said.
If this is not provided by the EPC, a bill of materials can be a good starting point to build a cyber security program, he said.
Owners should research which equipment vendors have self-reported vulnerabilities, as many have not, Franzino noted.
Operators can also use a number of tools to scan networks and produce inventories of devices and vulnerabilities, he said.
Risk control efforts might initially focus on network devices such as firewalls, switches and routers, seen as key risks to solar plants, Franzino said.
"Also focus on those connections you may have to other more un-trusted networks, whether it's back to your control center, or whether there is a way for you to connect from an office environment. And…think about that core server infrastructure that's running your SCADA system, that's running the brains of the operation."
System access
Solar farm owners should also perform a user account inventory to ascertain the access of all users within the system. Many users may not require the access they have been given, Franzino said.
"During construction and commissioning there's a whole host of people that need valid access to the sites... As you transfer operations, take a hard look at who has access and make sure you revoke access to those people that no longer need it," he said.
Solar plant employees must be made aware that phishing is the main method of cyber attack, through the use of social engineering enquiries, links and embedded files, Franzino said.
Password security remains a crucial factor and is often compromised by employees reusing passwords across multiple systems, he said.
"We are all too guilty of reusing passwords...It is one of the things that led to the successful turning off of the lights in the Ukraine attack.”
Security costs
The cost of cyber security management services provided by companies such as GridSME vary widely, depending on factors such as the size of the project.
For a smaller distribution grid project, simple patch management and basic cyber security services might cost between $5,000 and $10,000 per year, Franzino said.
Cyber security management for larger sites with networking components and SCADA infrastructure might cost $5,000 per month for full managed services including access management, patch management, among other provisions, he said.
UK average company investment in cyber security in FY 2016/17
(Click image to enlarge)
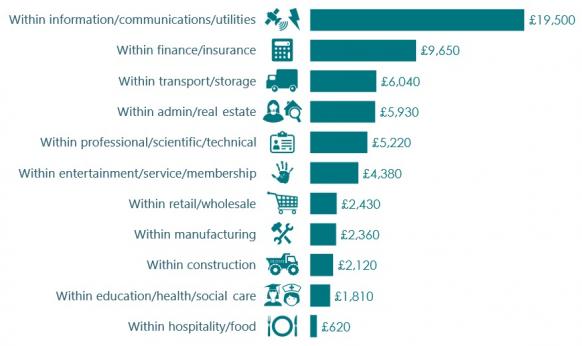
Source: UK government survey, conducted by Ipsos Mori.
When deciding on cyber security strategies, operators should take into account the cost of recovery as well as the cost of disruption, to plant operations as well as company reputation, Franzino said.
Costs can be reduced by proactive measures ahead of plant handover, such as implementing appropriate configuration management recovery plans which can avoid a lengthy plant outage from a system failure-- whether through a hardware fault, employee error, or cyber attack, Franzino noted.
"You should update those backup [system] images, but at least you can get the starting point for free by just requiring that as part of the handover package from your EPC," he said.
Going forward, increasing connectivity and grid efficiency will bring new challenges for cyber security.
For example, the Department of Energy (DOE) has identified cyber security as a key research area for new advanced inverter and power electronics designs, as part of its Grid Modernization Initiative research program.
"Advanced cyber security may be needed to ensure access-control, authorization, authentication, confidentiality, integrity, availability, and non-repudiation for the future smart grid," the DOE said in its recent tender document ‘Advanced Power Electronics Designs for Solar Applications.’
This could be through an encryption control imbedded at the foundational control microprocessor, which enables software control of grid forming functions “including voltage stability, frequency control and similar reliability and longevity requirements," the DOE said.
New Energy Update
